Over the past few years, Apple has enjoyed a stellar reputation for protecting the privacy of its users. iOS is the first major OS with built-in end-to-end encrypted messages and audio calls, and the Secure Enclave of iOS devices has been praised for its sophistication. In 2016, Apple successfully challenged an FBI demand to write new software that would let the FBI hack a locked iPhone, and in September 2017, Apple launched a new privacy website that made it easier to understand how Apple’s privacy policy affects users.
But even so, Apple still falls short in some ways in protecting user privacy. Here are a few steps Apple could take to maximize the privacy and security of its customers.
Encrypt Mail iCloud data at rest
TL;DR: Apple should catch up with Gmail by encrypting your emails at rest.
According to this table, data for most iCloud products is encrypted at rest. This means that while it’s stored on Apple servers, it’s encrypted with a key held by Apple, and anyone who hacks into the servers without the key can’t decrypt the data. However, iCloud Mail does not enjoy this protection. Instead, emails are stored completely unencrypted.
Apple provides an explanation for this: “Consistent with standard industry practice, iCloud does not encrypt data stored on IMAP mail servers.” But this is only “standard practice” because IMAP email came around during a time with low interest in privacy. Today, there is increasing interest in highly secure email services like ProtonMail and TutaNota. These services not only encrypt mail at rest, but they have modern encryption implementations that means that even the companies themselves cannot decrypt mail content. At this point, even Google encrypts Gmail emails at rest now. Apple should catch up with the rest of its competitors and store all emails encrypted at rest.
Let users disable WiFi per app
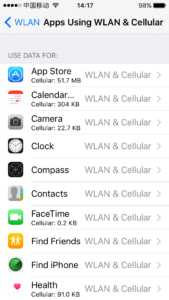
TL;DR: Apple lets users in China disable WiFi per app. They should let the rest of the world do that too.
As a developer, I am amazed by how well Apple has devised iOS to prevent unwanted apps from running on users’ devices. When it comes to malware, iOS is leagues ahead of Windows and Android, and even macOS and Linux. If you keep your iOS up to date, malware virtually won’t happen. When it comes to deleting apps, it’s a similar situation.
Simply by tapping that grey X on an app icon, you can delete an app completely, along with its notifications, background network activity, HealthKit access, everything. If you try to uninstall an app on macOS, it could be leaving a lot behind: kernel extensions, cache files, and even malware.
But as long as you want to keep an app on iOS, you are surprisingly limited in how you can control the app. An app has the ability to make network connections any time it is open! (And any time in the background, if Background Mode is enabled!) This can be used to share your IP with anyone, making it possible to estimate your location even if you haven’t agreed to give the app your location. It can even be used to identify you personally in some cases.
One easy way to fix this is to allow users to disable WiFi access per app. It is already possible to disable cellular data access per app by going to Settings → Cellular → Cellular Data. If we could disable WiFi access as well, we would have the power to choose which apps are and are not allowed to connect to the internet.
Provide an Apple-run VPN for new users
TL;DR: VPNs are useful privacy tools if used wisely. Apple should make its own VPN.
The internet of 2018 is a different place than it was just a few years ago. Starting in March 2017, ISPs are allowed to sell your internet browsing history to anyone they want to. And on April 23, the repeal of Net Neutrality will go into effect, which means that ISPs can also slow down certain sites that they don’t like.
If all of this sounds horrifying to you, luckily there is a respite for iOS: VPN apps. With a paid VPN service provided through an iOS app, you can route all of your internet traffic through the company running the VPN service. You can browse the internet just as before, but your internet provider will not be able to figure out what sites you’re visiting. Going even further, the sites you visit won’t be able to estimate your location or identify you from your IP anymore.
There are a few downsides to VPNs, however. One is that you need to trust that the VPN company isn’t doing anything shady with your internet data. Although I use a VPN that I trust, many VPNs (especially free ones) are objectively terrible. Another problem with VPNs is that knowledge of their benefits is not widespread.
What can Apple do about this? I propose that they could create their own VPN service. When a user buys an iOS device, they could be presented with this service during setup. This could cause the biggest increase in adoption of VPNs ever. When Apple launched iMessage in 2011 with end-to-end encrypted messages, millions of users got instantly upgraded to a much more secure messaging platform than SMS, and they didn’t even know it. The same could happen with an Apple VPN service.
This wouldn’t be the ultimate silver bullet to solving all internet surveillance problems, and it would involve placing additional trust in Apple to protect browsing history, but it would be a great step in the right direction.
Implement an iOS-wide VPN kill switch
TL;DR: iOS should block network connectivity if a VPN fails, until the user unblocks it.
The third-party VPN feature of iOS works well, but what happens if a VPN fails? In this case, apps connecting to the internet can suddenly connect without the VPN, which could compromise your privacy. On other operating systems, VPN companies provide apps with kill switches, which kill all connections if the VPN connection fails, until the user disables the VPN manually. Due to the nature of iOS, it is up to Apple to implement such a feature. Apple should add a kill switch feature to the the VPN feature of iOS, which would stop all network traffic if a VPN connection fails.
Tracking blocker for apps
TL;DR: Apple should let users block ads and trackers in apps.
In 2015, Apple took the unprecedented step of allowing third-party ad and tracking blockers for Safari in iOS. Whereas there was nothing before, it suddenly became possible to block third-party trackers, ads, sharing widgets in Safari. But Apple introduced no similar feature for blocking trackers in native apps. In fact, in 2017, Apple cracked down on apps that tried to indirectly block third-party trackers in apps.
If Apple is serious about user privacy, it would take the next step in allowing apps that block ads and trackers in Safari to also block them system-wide.
Add a light indicator to the front-facing camera

TL;DR: Apple should add a light indicator so that users knows when iPhone cameras are being used.
iOS excels in camera privacy when compared to macOS or other desktop operating systems. If you deny an app permission to access your camera, the app is completely cut off. But what happens if you press allow?
Last year, researcher Felix Krause shows that apps can use your camera in more ways than you expect. He showed how an app, given permission to use your camera, can use it at any point while you have the app open, even if you don’t see the camera preview, and don’t think it’s being used. His proof of concept video went viral.
Can Apple do anything about this? On Macs, they already have. Any Mac equipped with a camera also comes with a bright green light, which shines when the camera is in use. In the infamous 2010 Pennsylvania school camera spying case, students first discovered that their school was spying on them in their bedrooms using the camera of their school MacBooks by noticing the green LED camera light come on at unexpected times.
Apple could do something like this on iOS, and it doesn’t even have to be a physical light. By simply displaying a green dot on the corner of the screen, iOS can make it clear exactly when a camera is being used by an app.
Allow MAC address spoofing on iOS
TL;DR: Apple can squash NSA surveillance by implementing MAC address spoofing on iOS.
Each internet-connected device has a MAC address (short for “media access control address”). It is the address that your iOS devices use to identify themselves to WiFi access points. Without it, it wouldn’t be possible for multiple devices to connect to a single network. But MAC addresses have a serious drawback — they can be used to spy on you and track your movement. According to Edward Snowden, the NSA is capable of tracking the movement of everyone in a city by tracking the MAC address of their mobile devices.
The only way to protect against this is by MAC address spoofing. The privacy conscious operating system Tails OS already has MAC address spoofing as a feature. When Tails boots up, it doesn’t use the default MAC address. Instead, it creates a new, random MAC address that is used until the computer is turned off. In practice, this works well — Tails OS devices can still automatically connect to WiFi networks that were previously configured. If Apple wants to eliminate iPhone MAC addresses as a tool for privacy violation, they should implement MAC address spoofing.
Apple has taken many steps to protect its users. These measures would make its privacy efforts even more effective, and make the iPhone much closer to a true privacy-conscious device.

